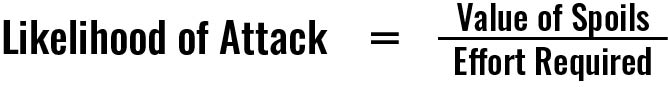Strictly Business: Securing the Digital Frontier
The FBI estimates bad actors (or “threat agents”) conduct over 4,000 ransomware (a type of malware) attacks per day. That is just one type of attack. Sometimes these people intend to steal or extort money. Sometimes they — as Alfred from the Dark Knight trilogy might say — "want to watch the world burn." Plus, because they change the techniques they use in trying to harm your organization and/or enrich themselves, the security world is always playing catch-up. In the face of such malicious behavior, how can an honest organization protect itself?
The first thing to do is to assess risk and understand what is at stake. Then, utilizing the organizational and industry standards and processes, the second thing to do is establish countermeasures to ensure application security.
Put generally, application security seeks to mitigate three types of risk. These types may result in direct and indirect losses of capital and/or revenue.
- The risk of application downtime
- The risk of information breaches and intrusion
- The risk of damaged reputation/goodwill
Application Downtime
- Work stoppage, which can result in lost revenue.
- Customer loss, which can result in reduced revenue.
Information Breaches and Intrusion
- Financial liability for failure to safeguard information.
- Loss of significant financially-valuable data.
- Legal liability for failure to adequately protect certain kinds of information.
Damaged Reputation/Goodwill
- Loss of customers/users.
- Loss of customer/user activity.
- Negative advocacy.
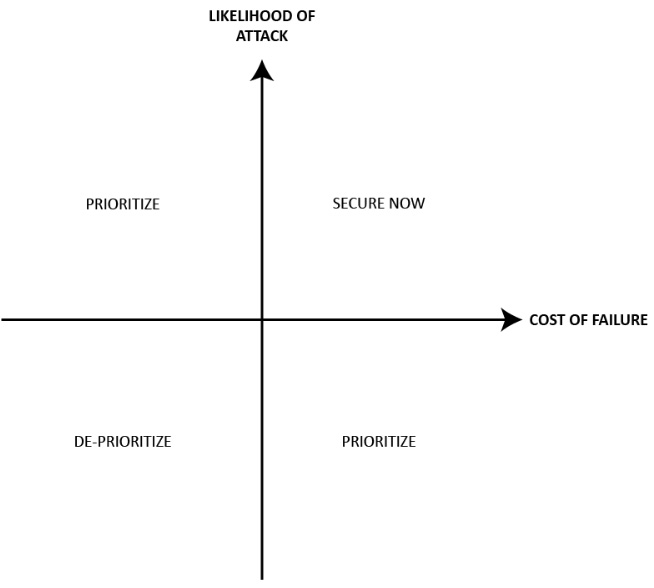
How do I prioritize security efforts?
Not everyone's security needs are the same. A bank protecting financial information or a hospital protecting health information has more stringent, complicated requirements (and certifications) than a personal blog, a marketing site with lead capture forms, or even an e-commerce site. Determining the level of security needed requires evaluating the value of what is vulnerable and the cost of application downtime or information breaches and intrusion.
Broadly speaking, prioritizing security efforts requires knowledge of vulnerabilities, the cost of security failures (including PR costs and cost to diagnose and recover from such failures), and how likely it is that someone would attack.
Even though each organization has its own needs, there are principles, standards and procedures that Insite follows to produce more secure applications.
Am I vulnerable?
If you have any digital assets, you have exposure. Nothing that has value is 100% safe, and with no shortage of bad actors ready to pounce on prey in the open, it is incumbent on every organization to evaluate their risks and harden the defenses where there is something of value to be stolen or held hostage, in order to reduce the likelihood of a successful attack.
There are no perfectly secure systems, only adequately secure systems relative to perceived threats.
What is vulnerable?
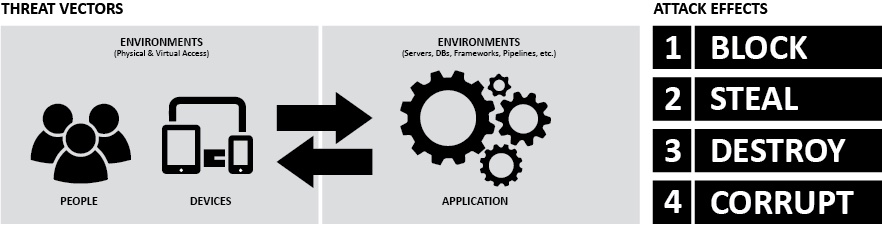
Anything of value that is in storage (at rest), on its way somewhere (in transit), or being processed in is a potential target for a threat agent. And there are numerous ways to attack, with every threat vector (routes people can use to attack or steal something valuable) imposing a potential burden on the organizations who need to protect their assets and the information of their customers or users.
Internal Threats
- Humans – Employees or other humans. Can be passive, volitional but not malicious, or intentional and malicious.
- Non-Humans – Hardware failure, dust, leaks
External Threats
- Humans – Hackers, espionage
- Non-Humans – Natural disasters, malware, power failure
Malicious attacks can occur from the user's physical or virtual environment all the way to the application itself, and everything connecting the components together. The net effect of these attacks could be to block access, or to steal, destroy, or corrupt information — because doing so presumably creates some perceived benefit to the attacker.
Top 10 Web Application Security Risks
The Open Web Application Security Project (OWASP) periodically lists the top 10 most common security threats. Organizations serious about protecting their site from vulnerabilities are wise to start here, as the majority of attacks fall into one of these threat categories. As of 2021, the top 10 security risks were:
- Broken Access Control
- Cryptographic Failures
- Injection
- Insecure Design
- Security Misconfiguration
- Vulnerable and Outdated Components
- Identification and Authentication Failures
- Software and Data Integrity Failures
- Security Logging and Monitoring Failures
- Server-Side Request Forgery (SSRF)
Protecting your organization from these threats requires regular security scans and mitigation, developer training, and staying up to date on current and emerging security threats.
Principles
The 5 core functions of the National Institute of Standards and Technology (NIST) framework for infrastructure cybersecurity are Identify, Protect, Detect, Respond, and Recover.
Identify – Facilitate full visibility of all physical and digital assets, as well as how they are connected, along with defined roles and responsibilities to understand risks and exposure before you can put procedures in place to manage those risks.
Protect – Employ reasonable rules, processes, and other measures to protect or contain the impact of sensitive information and systems. This includes awareness training and controlling access to digital and physical assets, as well as using protective technology.
Detect – Institute automatic and manual safeguards that regularly scan, log, check for, and report potential vulnerabilities, attacks, and/or breaches throughout the software development lifecycle.
Respond – When a breach or vulnerability is detected, a response team needs to be in place to close the breaches, assess and limit the damage, and notify affected users and appropriate authorities in a timely manner.
Recover – Once a breach has occurred, an organization must restore capabilities or services that were lost as a result of this breach.
Conclusion
In a rapidly evolving digital landscape, safeguarding sensitive information transcends the realm of an organization's IT department. Cybersecurity demands the attention and diligence of every individual, from contractors to employees to executives. With data breaches and cyber threats on the rise, all stakeholders must recognize their crucial role in fortifying defenses. From governance and training to active testing and scanning, to issue location and mitigation, embracing a collective responsibility mindset will help your organization navigate the perilous cyber realm and protect what truly matters.